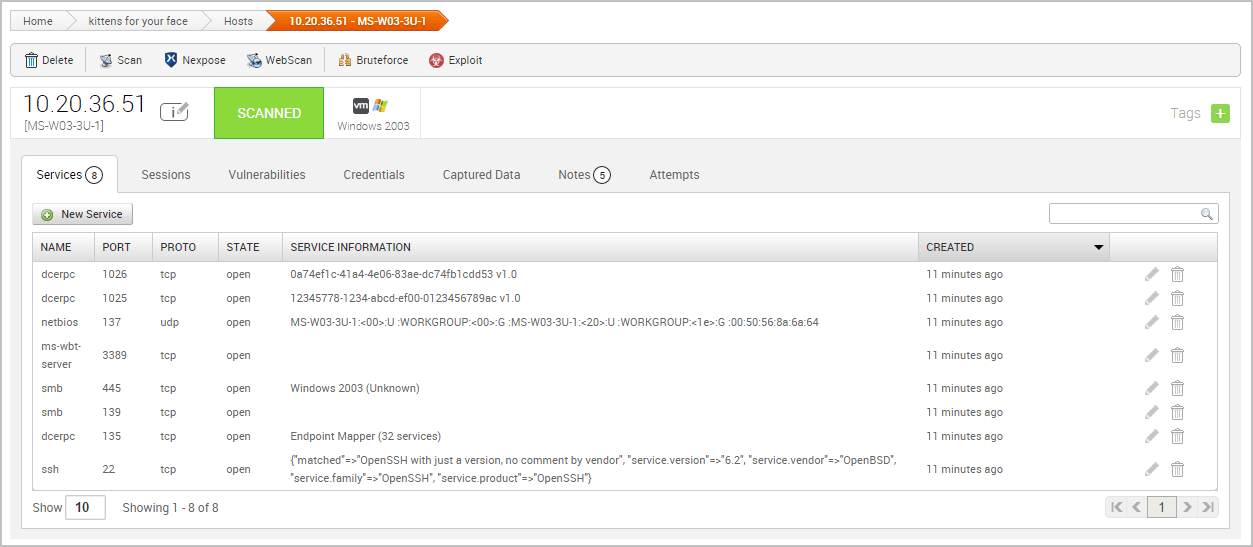
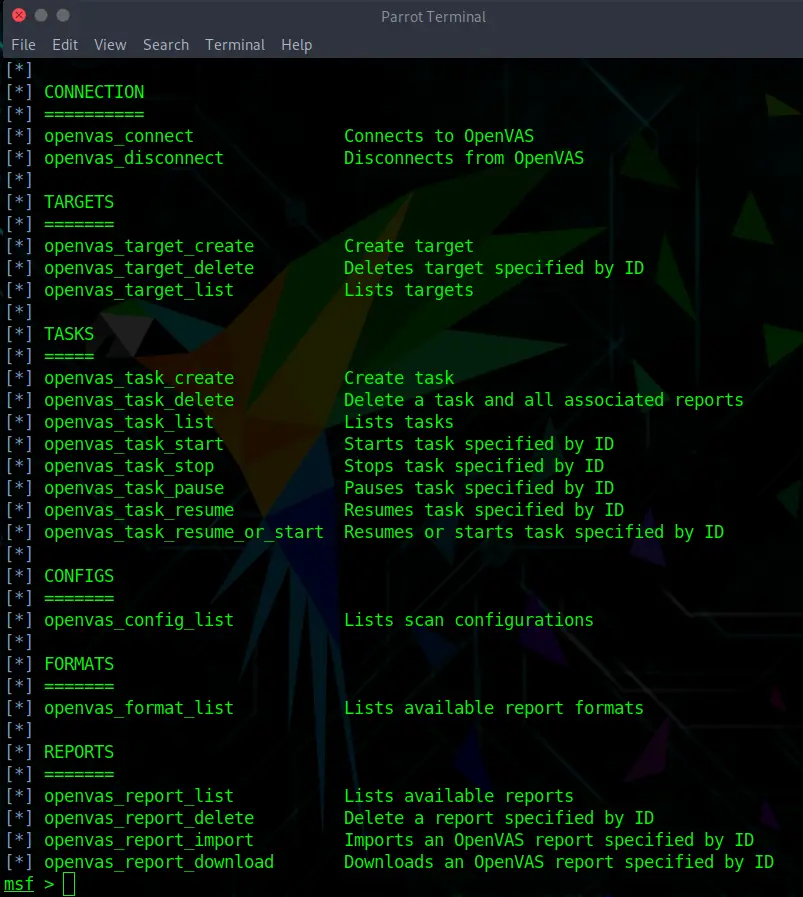
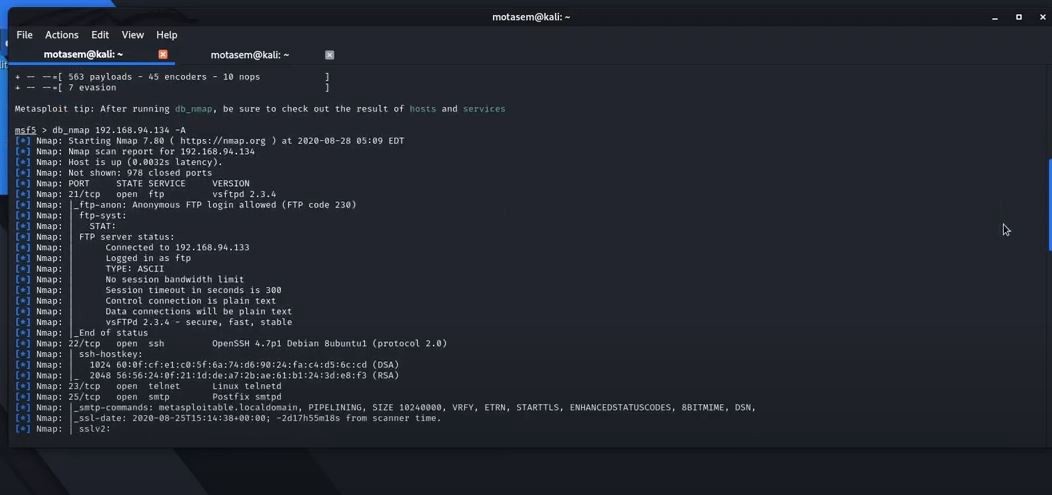
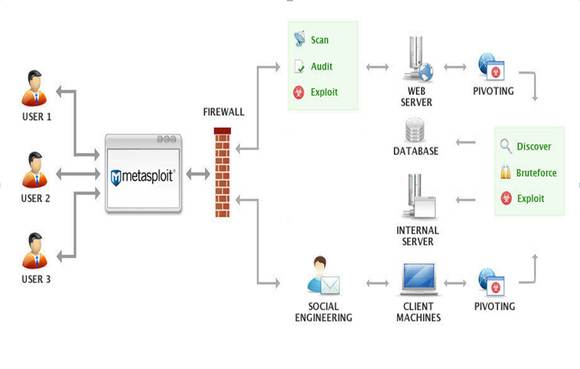
Metasploit Cheat Sheet by binca - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion
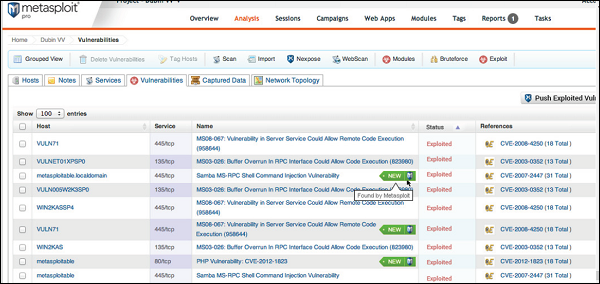
![Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book] Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/library/view/metasploit-revealed-secrets/9781788624596/assets/15d23931-4396-4e2e-8b6e-6c4a90c7f021.jpg)
Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]
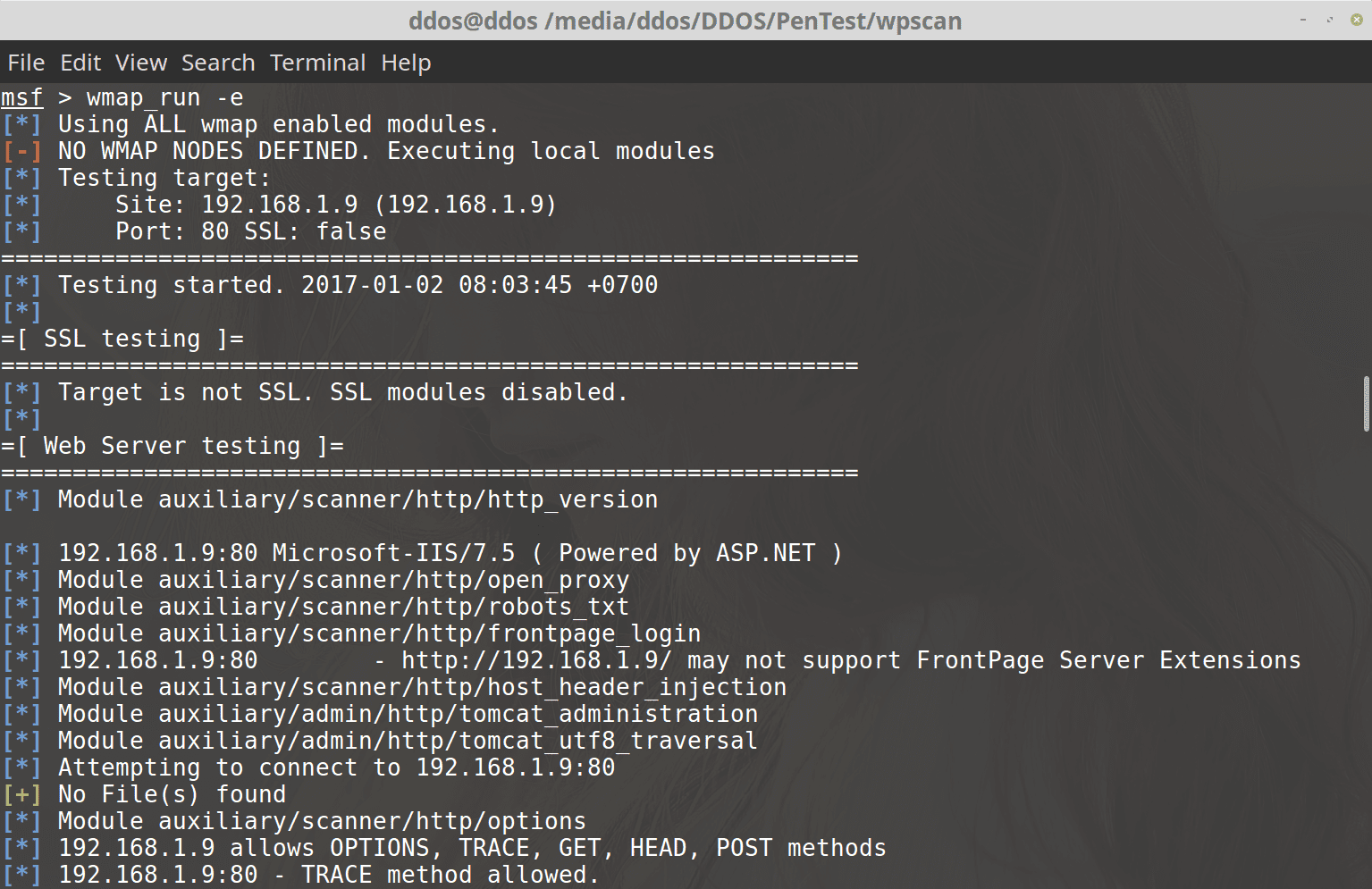
![Exploiting the vulnerability using Metasploit - Hands-On Web Penetration Testing with Metasploit [Book] Exploiting the vulnerability using Metasploit - Hands-On Web Penetration Testing with Metasploit [Book]](https://www.oreilly.com/library/view/hands-on-web-penetration/9781789953527/assets/d2bc9cb7-fbaa-453f-860a-5b6740bd759e.png)







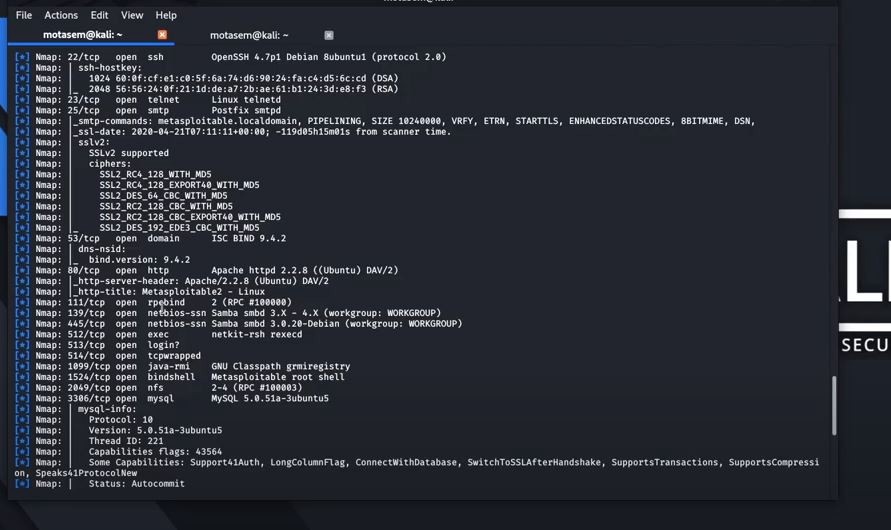

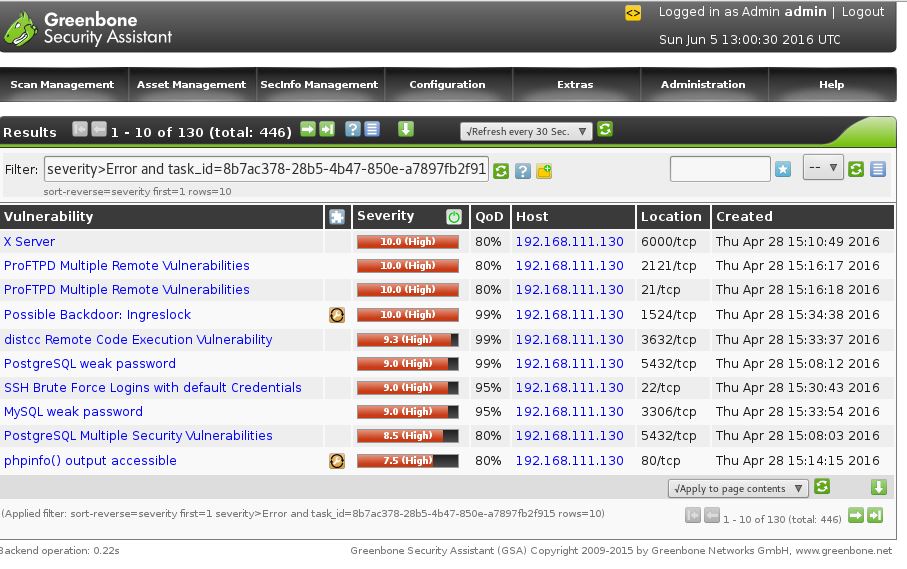
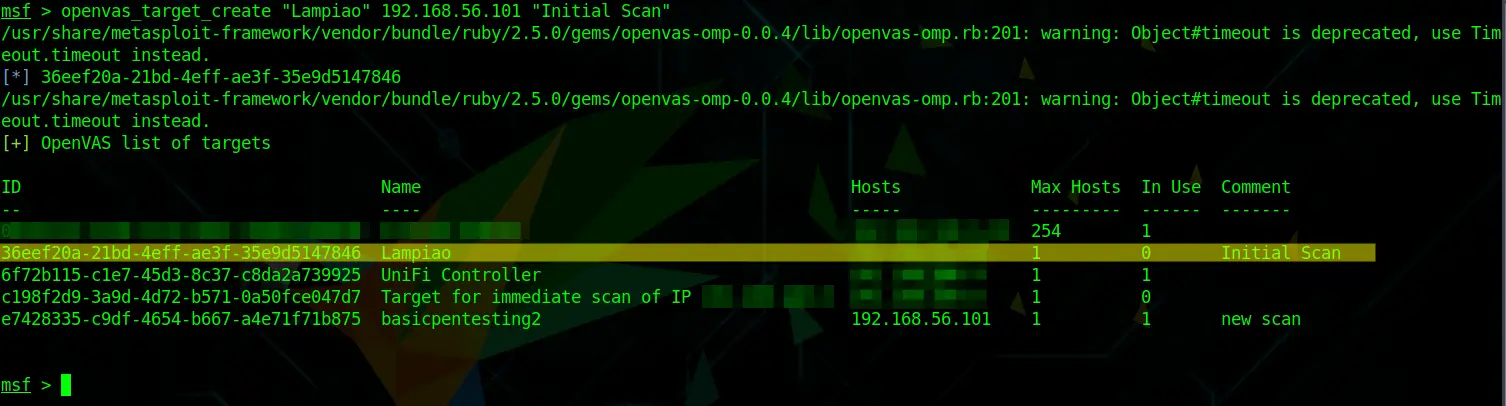
![Importing scan results - Hands-On Web Penetration Testing with Metasploit [Book] Importing scan results - Hands-On Web Penetration Testing with Metasploit [Book]](https://www.oreilly.com/library/view/hands-on-web-penetration/9781789953527/assets/8844d50f-3488-45ce-8726-db827425b59f.png)